
Get Started
Hydraledger gives you full control of your digital life!
- built with modularity in mind
- blockchain and backend-agnostic
- with latest cryptographic protections
- open-source and free with no barriers to entry
- complete internet stack of different protocols
TAKE FULL CONTROL OF YOUR DIGITAL LIFE!
IOP provides self-sovereign identity (SSI) allowing multiple independent private personas. You can create and witness claims about personas and also share only the requested parts of such claims for verification, letting you securely manage every aspect of your life. Hydraledger's technology is open source and available for anyone. Although IOP is dedicated to providing a complete solution to the problems of online identity and privacy, Hydraledger is fully modular without vendor lock-in. Users and businesses are free to use and combine any part of the stack they want.
OPEN

Anyone can run a node, earn Hydra tokens, and help revolutionise our digital world.
FAIR

Mobile phones plus Hydraledger technology will give billions of people access to fundamental services.
TRUSTLESS

Hydraledger eliminates the need to entrust your data to third parties, many of which accumulate unfair political and financial power.
PRIVATE

Our technology gives you complete control over what information you share and with whom.
SIMPLE

Unlike most blockchain technologies, Hydraledger is simple and user-friendly by design.

An Identity Problem
Our identity is a combination of both abstract and specific pieces of information. In the offline world, proving something like age, nationality, or a qualification is as simple as presenting a physical document to a human who uses their judgement to assess its authenticity. But the need for human discretion comes at great economic, social, and political cost.
Attempts to digitise and automate the process have created an array of far more serious problems. Unless you’re using cryptographic proofs of key control, it is almost impossible to prove the validity of any information in the virtual world without the assistance of a trusted authority. Neither party can be certain with whom they’re communicating, nor can the recipient be sure that a sent document is genuine.


Privacy Laid Bare
In both online and offline processes, users have no fine-grained control over the sharing of specific pieces of data, nor can they grant and revoke access at will. Due to the limited number of accepted credentials, users are forced to overshare data (e.g. using a passport to verify drinking age) which unnecessarily compromises their privacy. Privacy is further eroded in the online process where one-click sign-ons have become common and grant the provider access to even more personal data which, once shared, can not easily be retracted.
All of this data needs to be carefully transmitted and stored, which gives rise to immense costs related to cybersecurity and data compliance. These costs are inevitably passed on to the consumer in the form of monetisation of our data. That brings us to the gatekeepers and intermediaries of which systems based on a central root of trust must rely.
Unsecure, Unethical Gatekeepers
Centralised reputation systems rely on massive datasets which have proved an irresistible and relatively straightforward target for hackers. Data breaches such as the 2017 Equifax hack, which saw the theft of 147 million peoples’ personal data have become commonplace. Many of these gatekeepers have also been found to abuse their position with inconsistent and unethical behaviour which impacts billions of people globally who take access to these services for granted.
Due to factors such as cost, remoteness, and unfair governance, billions more are denied identity and credential services which form the fundamental basis of banking, healthcare, and civil rights.
Attempts have been made to use existing technologies and new blockchain-based solutions to address all of these challenges, but they have so far proven to be insufficiently fast, secure, or scalable. Furthermore many still rely on trusted third parties. Even the latest decentralised technologies based on Bitcoin’s Proof of Work and more recent versions using Proof of Stake.

Our Solution
Our Decentralized Solution
IOP’s solution is a decentralised trust ecosystem based on self-sovereign identifiers and secure peer-to-peer communication. The Hydraledger Stack is a multi-layered platform which combines a public and permissionless blockchain secured by a state-of-the-art consensus mechanism with a number of modular and user-friendly tools that enable the creation of an ecosystems of dApps and decentralised services. The core components of our stack are being created in the Rust programming language, which guarantees memory safety and thread safety using compile-time checks with zero runtime overhead to prevent common and serious bugs. However additional tools will also be provided to allow applications to be built using more familiar programming languages.
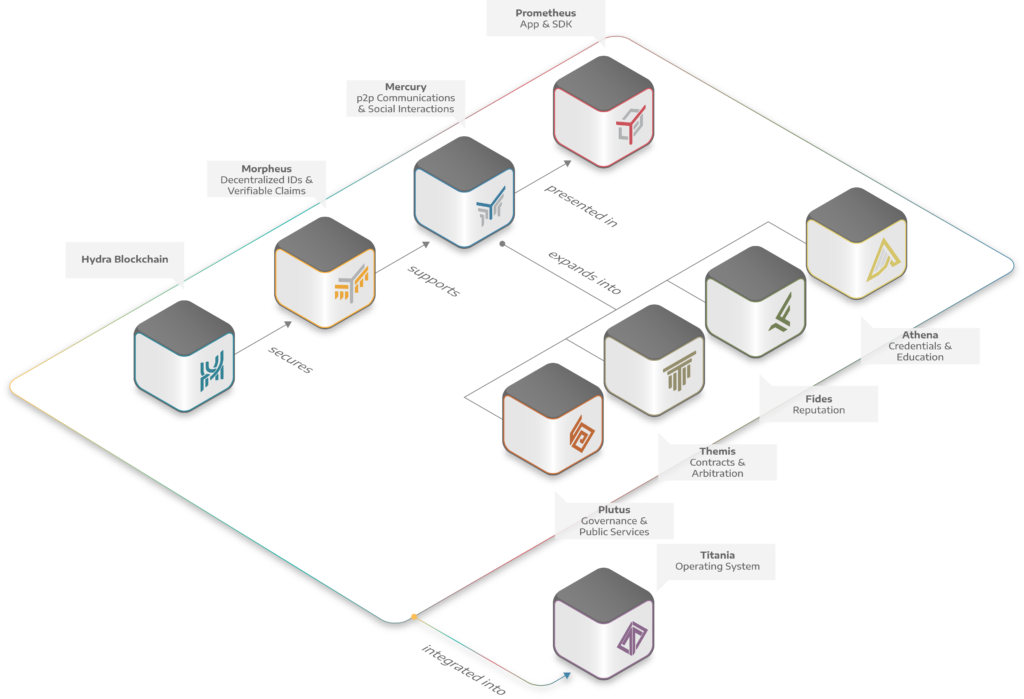
Hydra is built on an open and permissionless Delegated Proof of Stake consensus. In this consensus, the users of the system use their stake to elect a committee of 53 representatives that are responsible for maintaining and extending the blockchain. As well as participating in consensus, network nodes will enable Mercury’s peer-to-peer communication, and provide secure data storage and claim verification services to users.
Nodes are rewarded for their services in Hydra tokens. There are no lock-up conditions or thresholds for the number of tokens a user needs to vote. The likely need for businesses to manage thousands of keys for different DIDs will create token liquidity and a powerful incentive for nodes to participate in the ecosystem.
Self-sovereign identity is of limited use without a means of granting access to claim issuers and verifiers. Mercury is an encrypted, two-way authenticated peer-to-peer communication protocol which enables the claims process, among many other use cases. Mercury is a decentralised web of Home nodes which punch through the Network Address Translation layers. Nodes are chosen based on trust and reliability effectively forming a decentralised, secure cellular network which enables peer discovery.
Mercury ensures no data is leaked during claim verification or any other type of communication, and is the ideal tool for dApps which require secure, direct user connections. If you’d like to learn more about Mercury, please visit our IOP GitHub account where we’ve published a prototype of the protocol.

Limitless Possibilities
IOP technology creates a decentralised global web of trust open to all. We see the various constituent technologies as powerful and flexible enough to be applied far beyond identity and claims verification to decentralised services which serve organisations, communities, and societies.
By focusing on simplicity, ease of use, and low cost, the IOP ecosystem is ripe for mass adoption and can create opportunities for billions of users across the globe. In turn, those new audiences represent new opportunities for business, as well as developers whose apps can transform sectors as diverse as social media, digital advertising, peer-to-peer content, and data integration.
IOP’s secure, private, censor-resistant, and decentralised technology enables maximum privacy, minimal disclosure, and aligns perfectly with the coming shift towards greater user power. Thanks to the Hydra consensus, IOP is a fast, efficient, cost-effective, scalable, and democratic technology.
The IOP Stack allows developers to harness and build upon any aspect of the technology by being modular, extensible, portable, and accesible. By ensuring that our code is open-source and well documented, we encourage developers to discover our solutions and contribute to our vision of a better digital world.


